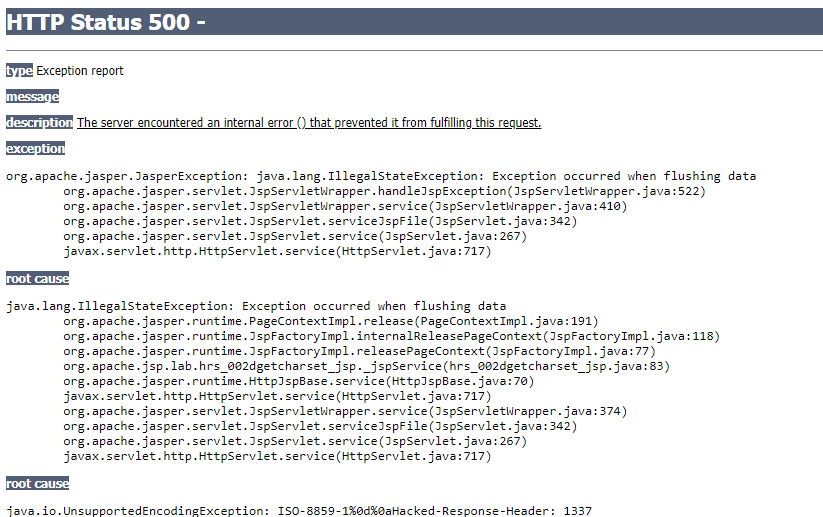
.extra https://docs.djangoproject.com/en/2.0/ref/models/querysets/#django.db.models.query.QuerySet.extra For example, this use of extra(): >>> qs.extra( ... select={'val': "select col from sometable where othercol = %s"}, ... select_params=(someparam,), ... ) is equivalent to: >>> qs.annotate(val=RawSQL("select col from sometable where othercol = %s", (someparam,))) .raw https://docs.djangoproject.com/en/dev/topics/db/sql/ >>> for p in Person.objects.raw('SELECT * FROM myapp_person'): ... print(p) John Smith Jane Jones .execute do_sql from django.db import connection cursor = connection.cursor() cursor.execute('insert into table (column) values (%s)', (dinosaur,)) cursor.close() from handy.db import do_sql do_sql('insert into table (column) values (%s)', (dinosaur,)) RawSQL >>> from django.db.models.expressions import RawSQL >>> queryset.an...