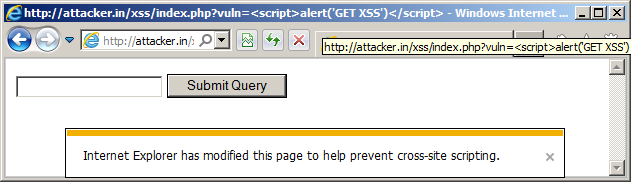
XSS: Gaining access to HttpOnly Cookie in 2012

Update 2016/02: We were asked by a lot if this still works. Shortly after our disclosure, this issue has been patched. ------ The Background - The Past Gaining access to HttpOnly cookie was first attempted by means of XST, Cross Site Tracing vulnerability. Soon after the popularity of XST, the TRACE method has been disabled by most web servers. Later, browsers' implementation of XMLHttpRequest also blocked "TRACE" method (i.e. xmlhttp.open('TRACE', url, true) ]. Later, a flawed implementation in Firefox's XMLHttpRequest which can be used to access set-cookie response header was fixed. JS Debugger pointing out "TRACE" method as invalid arugment JS Debugger pointing out "TRACE" method as illegal value A Sla.ckers.org forum member, LeverOne, posted ways to access HttpOnly cookie through the use of Java API and applet. I reproduced his techniques. When the first method was tried, the J...